Marcus Hutchins

Marcus Hutchins
Personal Life and Interests
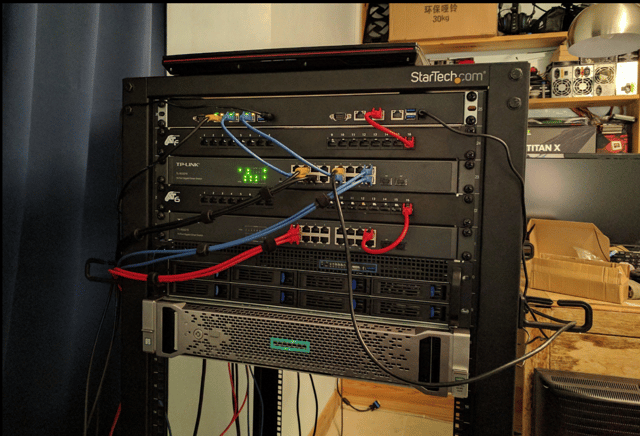
ESXi server and Necurs.
Though his name has not been revealed to the world as of yet, he has given insight about his life on is Twitter handle. [6]He was born in June 1994 in the United Kingdom to English and Scottish parents - that is, he is half Scottish. [4]
He currently lives in South-West England in a Victorian House.
He is considered a tech nerd and has amassed a huge collection of video games that he has shared with the world.
He has also shared the kind of servers that he uses, his computers screens and ideas about IT on his Social media profiles. [4]
He often attends "Hack conventions" such as the one he attended the previous summer, in Las Vegas, Nevada called Defcon. [6]
Education

Malware Tech's gaming equipment.
Besides having a primary and secondary education, he opted not to attend University and continue his higher education as he was offered a job in security as an IT executive.
His education in tech and web security and IT is all self-taught.
He now offers his services to a private intel threat firm in Los Angeles, California. [4]His job consists of investigating the latest malicious computer software released by criminals and hackers. [4]
Cyber Ransom
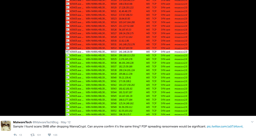
Malware Tech's cell phone getting blasted with messages from Twitter and beyond.
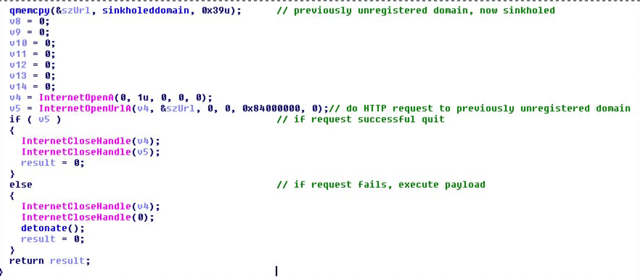
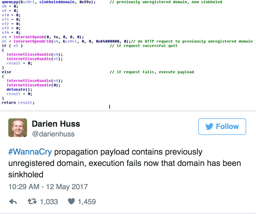
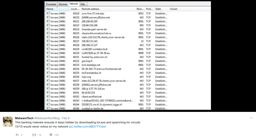
The code he shared of the domain sinkhole.
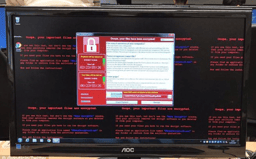
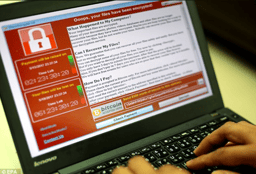
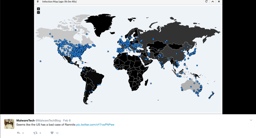
May 12th, 2017, a cyber attack known as WannaCrypt attacked IT Managers and major companies around the world.
On the morning of Friday, May 12th, 2017, which was another day off for Malware Tech, he woke up just before the afternoon and checked the UK cyber threat sharing platform and began following the spread of the Emotet banking malware.
When he returned from lunch with a friend, he checked again by now the ransomware was at full swing.
Look for unregistered or expired C2 domains belonging to active botnets and point it to our sinkhole (a sinkhole is a server designed to capture malicious traffic and prevent control of infected computers by the criminals who infected them).He
discovered that it included an unusual reference to a website address that nobody owned, so he purchased the address for £8.30 and pointed it at a ‘sinkhole’ server in Los Angeles. With
the help of other IT experts, they took to eradicating the malware. He
followed his standard model of taking three steps, which are: [9]
Gather data on the geographical distribution and scale of the infections, including IP addresses, which can be used to notify victims that they’re infected and assist law enforcement.
Reverse engineer the malware and see if there are any vulnerabilities in the code which would allow us to take-over the malware/botnet and prevent the spread or malicious use, via the domain we registered.
Unexpectedly, his registration of the website prevented the spread of the ransomware and prevented it ransoming any new computer.
They triggered the malware by accident and realized what they have done and kept it online in order to kill the rest of the infections.
He is being regarded as a hero, yet he says that it was done by accident as he was just following his own protocol in IT work which led him to discover and see the answers to stopping the problem which then became obvious in halting immediately.
Malware Tech believes that such hackers have no reason to ever stop as there's a lot of money to be made.
The next hack may not be as easy to stop.