RAGNAR LOCKER

RAGNAR LOCKER
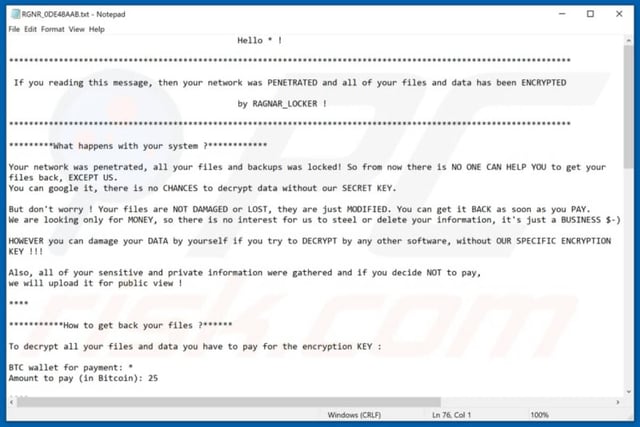
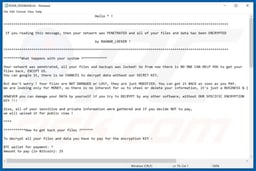
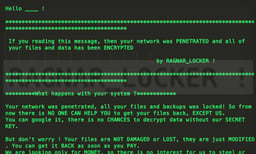
Ragnar Ransom Letter
RAGNAR LOCKER (first spotted December 2019) is a group and a ransomware software that focuses their attacks on corporate entities to steal information and hold it for ransom.[1][2]
History
Towards the end of December 2019, attackers first began using the Ragnar Locker as a way to attack compromised networks.[8]
On November 2, 2020, Japanese Gaming Giant, Capcom, came under attack by the malware affecting certain systems including email and file servers. On November 9, 2020, Ragnar Locker succeeded in downloading 1 terabyte of information from Capcom, including the personal information of employees and customers. The attackers demanded contact and 1.1 billion yen in Bitcoin by November 11, 2020.[10]
Hacking Techniques
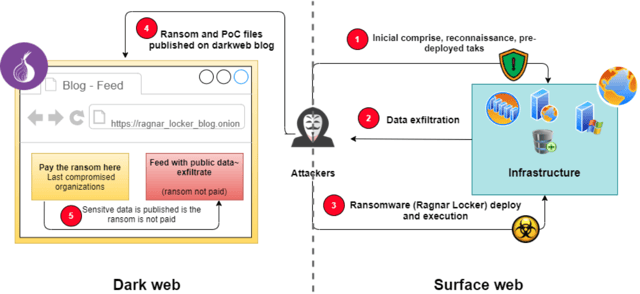
Ragnar Locker Infection Chain
Attacking Windows Remote Desktop Protocol (RDP) to gain a foothold in networks.[2]
Exploiting managed service providers' remote management software for network access.[2]
Gaining administrative-level access to domains.[2]
Using native Windows administrative tools for lateral movement to Windows clients and servers.[2]
The method they use to execute attacks is known as Living-of-the-Land, which helps in bypassing security software detection.[2]
How it works
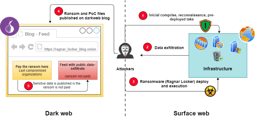
Every time an infrastructure is infiltrated, Ragnar Locker operators follow a list of steps.
Before starting, the attackers will inject a module capable of collecting data from infected machines and upload it to their server.
Then they will notify the target the files will be released to the public if they do not pay their ransom.[5]
The attackers will then compromise networks, infrastructures and organizations using vulnerabilities found, or social engineering (security) through phishing attacks, spearphishing, or backward error corrections (BEC).[5]
Once the data exfiltration process and compromise process are complete, the ransomware deploy is performed manually.[5]
When the ransomware starts, it lists running processes and stops if these services contain specific strings.
This disables some services as a way to bypass security protections, along with database and backup systems, which increases the impact of the attack.[5]
The data encryption malware then infects computers based on the Windows language settings.
The malware will terminate the process if the setting is configured as one of the former Soviet Union countries.[5]
The encryption process will begin after that.
When this is happening, Ragnar Locker will skip folders, files, and extensions with certain names.
This reveals that the malware is impacting security professionals and anyone that uses the specific web browser to navigate the dark web.[5]
Ragnar will then add the extension ".ragnar_" to the end of a file name and "" will be replaced by a generated and unique ID. All the available files are encrypted and the notepad.exe process is opened showing the ransom note file. The ransom note file starts with "RGNR_*" and is appended to the encrypted files.[5]
To encrypt the files, Ragnar receives and decodes the ransom note from the.keys section.
The section is then decoded in runtime.[5]
When a file is encrypted, the "RAGNAR" file marker is added to the end of the file.[5]
Inside the malware is a hardcoded link to a page with a countdown and the process to pay the ransom.[5]